- cross-posted to:
- artificial_intel@lemmy.ml
- fuck_ai@lemmy.world
- security@lemmy.ml
- cross-posted to:
- artificial_intel@lemmy.ml
- fuck_ai@lemmy.world
- security@lemmy.ml
Q. Is this really as harmful as you think?
A. Go to your parents house, your grandparents house etc and look at their Windows PC, look at the installed software in the past year, and try to use the device. Run some antivirus scans. There’s no way this implementation doesn’t end in tears — there’s a reason there’s a trillion dollar security industry, and that most problems revolve around malware and endpoints.


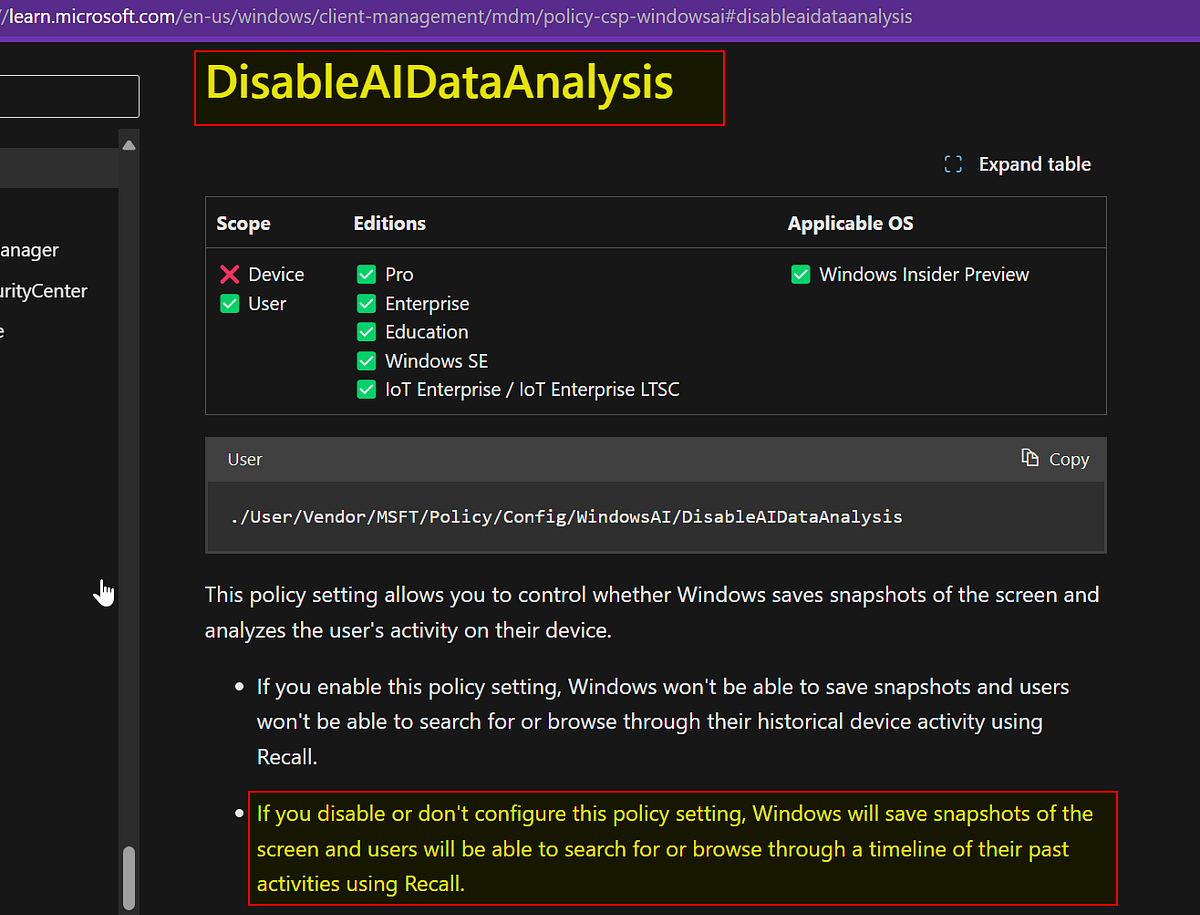
“If sensitive information is not saved” is doing a lot of heavy lifting for you there. The issue is that it saves everything.
But it doesn’t save completely everything. It does snapshots as far as I understand. So it’s unlikely a whole password would be there on a snapshot. And again, it had to be mentioned that anything can be excluded from recall or disabled completely.
At this point it has to be again highlighted that gaining access to a computer is very hard and that in itself is game over scenario. More information can be gained from a keylogger than this recall feature.
A keylogger isn’t retroactive to before the keylogger was installed though. Recall is. Also, with Recall you don’t need to write keylogging software and get it past antimalware scans (and keep it from getting detected), you just have to get an infostealer past them one single time to take the Recall database.
It’s very unlikely you could get the password from recall
The video posted by Moorshou literally shows someone getting a password and a credit card number from it. Yes, the password was due to someone clicking the show password button momentarily but do we just never expect people to use those or to not use a password manager that would show the password on screen at some point? Due to it doing text recognition, you would literally be able to just search for “credit card” to find all the times when it was displaying a credit card field on a checkout page or “password” to find all the times someone is logging in or using their password manager. And that’s using the built in search, not even exfiltrating the data and processing it with more specialized tools.
You really need to watch that video to see what it can do and how easily it can do it.
So even if it does ship like this guy thinks it will, it will take someone gaining control of the computer and having the victim click show password at the wrong time.
The end is nigh.
https://github.com/xaitax/TotalRecall
User python script. Full control of computer not required.
And how does the python script run itself?
How does any virus run itself? Are you seriously this dense?
Hint: there are many attack vectors, including no-click drive-by downloads, programs from Softonic, etc.
EDIT: Does this person seriously believe that because Microsoft made it, it must be secure, despite that literally having just been proven wrong? And that pointing that out means I need to be smarter than everyone at MS? That explains the delusional argument they’re going with.
??? It saves everything it sees that’s the point ???
Not the same as a snapshot.
Eric Parkers video Recall
Here is an alternative Piped link(s):
Eric Parkers video Recall
Piped is a privacy-respecting open-source alternative frontend to YouTube.
I’m open-source; check me out at GitHub.